고정 헤더 영역
상세 컨텐츠
본문
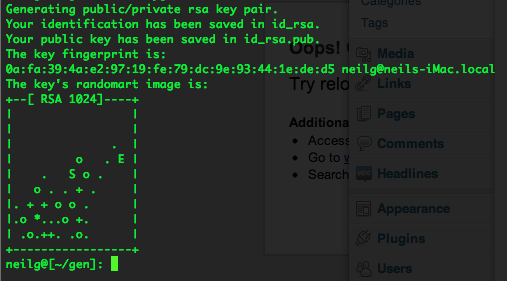
Python OpenSSL generating public and private key pair. Ask Question Asked 7 years, 11 months ago. Active 6 months ago. Viewed 11k times 3. I am having problem finding a command that would generate a public and private key pair using OpenSSL. Could someone show me some example code of this in action.generatekey(type, bits) Generate a.
-->
To sign an assembly with a strong name, you must have a public/private key pair. This public and private cryptographic key pair is used during compilation to create a strong-named assembly. You can create a key pair using the Strong Name tool (Sn.exe). Key pair files usually have an .snk extension.
Generating Public And Private Keys In Python Florida
Note
In Visual Studio, the C# and Visual Basic project property pages include a Signing tab that enables you to select existing key files or to generate new key files without using Sn.exe. In Visual C++, you can specify the location of an existing key file in the Advanced property page in the Linker section of the Configuration Properties section of the Property Pages window. The use of the AssemblyKeyFileAttribute attribute to identify key file pairs was made obsolete beginning with Visual Studio 2005.
Create a key pair
To create a key pair, at a command prompt, type the following command:
sn –k <file name>
Mar 19, 2020 TrueLicense is an open source engine for license management on the Java Virtual Machine. The user has to enter a license key and the product needs to check if it is valid or not. Open Source License generator plugin for products on the IntelliJ platform. Serial Key Generator is application specially designed for software developers to help protect your applications by serial key registration. Button above will open a connection to a third. May 11, 2018 License4J comes with License Manager GUI application to generate and store software license files and cryptographically secure serial numbers. License4J Auto License Generation and Activation Server is a web application which handles license generation, auto activation, manual activation, deactivation, online key validation and blacklist check. Older articles about license verification spend a lot of brainpower on 1) encoding information in the limited-length license key, such as a maximum app version, and 2) on partial key verification. If we drop the requirement that license keys be easy to type, we can get a simpler and more secure solution. Jul 11, 2014 License GNU General Public License version 2.0 (GPLv2) Follow Free Key Generator. Free Key Generator Web Site. Other Useful Business Software. Fast, Integrated Design and Development for Modern Apps. Get latest updates about Open Source Projects, Conferences and News. License key generator open source.
In this command, file name is the name of the output file containing the key pair.
The following example creates a key pair called sgKey.snk.
If you intend to delay sign an assembly and you control the whole key pair (which is unlikely outside test scenarios), you can use the following commands to generate a key pair and then extract the public key from it into a separate file. First, create the key pair:
Next, extract the public key from the key pair and copy it to a separate file:
Once you create the key pair, you must put the file where the strong name signing tools can find it.
When signing an assembly with a strong name, the Assembly Linker (Al.exe) looks for the key file relative to the current directory and to the output directory. When using command-line compilers, you can simply copy the key to the current directory containing your code modules.
If you are using an earlier version of Visual Studio that does not have a Signing tab in the project properties, the recommended key file location is the project directory with the file attribute specified as follows:
How Public And Private Keys Work
See also
-->Creating and managing keys is an important part of the cryptographic process. Symmetric algorithms require the creation of a key and an initialization vector (IV). The key must be kept secret from anyone who should not decrypt your data. The IV does not have to be secret, but should be changed for each session. Asymmetric algorithms require the creation of a public key and a private key. The public key can be made public to anyone, while the private key must known only by the party who will decrypt the data encrypted with the public key. This section describes how to generate and manage keys for both symmetric and asymmetric algorithms.
Symmetric Keys
The symmetric encryption classes supplied by the .NET Framework require a key and a new initialization vector (IV) to encrypt and decrypt data. Whenever you create a new instance of one of the managed symmetric cryptographic classes using the parameterless constructor, a new key and IV are automatically created. Anyone that you allow to decrypt your data must possess the same key and IV and use the same algorithm. Generally, a new key and IV should be created for every session, and neither the key nor IV should be stored for use in a later session.
To communicate a symmetric key and IV to a remote party, you would usually encrypt the symmetric key by using asymmetric encryption. Sending the key across an insecure network without encrypting it is unsafe, because anyone who intercepts the key and IV can then decrypt your data. For more information about exchanging data by using encryption, see Creating a Cryptographic Scheme.
The following example shows the creation of a new instance of the TripleDESCryptoServiceProvider class that implements the TripleDES algorithm.
When the previous code is executed, a new key and IV are generated and placed in the Key and IV properties, respectively.
Sometimes you might need to generate multiple keys. In this situation, you can create a new instance of a class that implements a symmetric algorithm and then create a new key and IV by calling the GenerateKey and GenerateIV methods. The following code example illustrates how to create new keys and IVs after a new instance of the symmetric cryptographic class has been made.
When the previous code is executed, a key and IV are generated when the new instance of TripleDESCryptoServiceProvider is made. Another key and IV are created when the GenerateKey and GenerateIV methods are called.
Asymmetric Keys
The .NET Framework provides the RSACryptoServiceProvider and DSACryptoServiceProvider classes for asymmetric encryption. These classes create a public/private key pair when you use the parameterless constructor to create a new instance. Asymmetric keys can be either stored for use in multiple sessions or generated for one session only. While the public key can be made generally available, the private key should be closely guarded.
Opt to take Ignis with you - he moves more slowly than usual so you'll have to keep to his pace, but you'll need him so there's no point making a fuss. Ff15 chapter 10 generator key. Fodina Caestino MineThe enemy types in the Fodina Caestino Mine vary by time of day, so you will either face pockets of Gurangatches (weak to Broadswords, Guns and Ice, resistant to Fire) or Snagas (weak to Javelins, Daggers and Fire, resistant to Ice).Clear the lake of enemies and then make your way around the left hand side and down the slope. Fodina Caestino MinesDeal with the enemies near the hut and collect the key, then make your way to the two generators - the first is guarded by a Gigantoad (weak to Javelins, Mechanisms, and Ice, and resistant to Lightning), and the second is back at the lake where you started.Once power is restored and the way forward is clear it may be worth camping now to make sure you're in top condition, and there are also a number of treasures and potions tucked away in the rest of the map as well as some elemental essences to absorb, so you may want to take a quick tour around the rest of the area. Once you're ready make your way to the marker - on the way Gladio will pick a fight with you, but if you stand up for yourself you'll get a temporary 50% boost to vitality.Clear the lake of enemies and then look at the tomb entrance to trigger a fight against Malboro. Your path is blocked so you'll need to retrace your steps and take a look at the control panel.Follow the markers down the slope and around the path - there's a campsite on your left just before you reach the far end, but it's worth waiting for later to camp unless you really need to do so now.
A public/private key pair is generated whenever a new instance of an asymmetric algorithm class is created. After a new instance of the class is created, the key information can be extracted using one of two methods:
The ToXmlString method, which returns an XML representation of the key information.
The ExportParameters method, which returns an RSAParameters structure that holds the key information.

Both methods accept a Boolean value that indicates whether to return only the public key information or to return both the public-key and the private-key information. An RSACryptoServiceProvider class can be initialized to the value of an RSAParameters structure by using the ImportParameters method.
Asymmetric private keys should never be stored verbatim or in plain text on the local computer. If you need to store a private key, you should use a key container. For more on how to store a private key in a key container, see How to: Store Asymmetric Keys in a Key Container.
Generating Public And Private Keys In Python File
The following code example creates a new instance of the RSACryptoServiceProvider class, creating a public/private key pair, and saves the public key information to an RSAParameters structure.




